Impressive Tips About What Is The Difference Between ATS And STS

STS ATS Which Is Better For Critical Equipment Electrical
Decoding the Acronym Soup
1. Applicant Tracking Systems vs. Security Token Service
Ever feel like the tech world is just throwing alphabet soup at you? You're not alone! Two acronyms that often get mixed up are ATS and STS. While they sound similar, they operate in entirely different galaxies. One's about finding the perfect employee, and the other's about securing digital assets. Lets dive in and untangle this acronym confusion with a bit of clarity and, hopefully, a chuckle or two along the way.
Let's start with ATS. An Applicant Tracking System is essentially a software solution that companies use to manage the entire hiring process. Think of it as a digital filing cabinet (on steroids!) for job applications. It helps recruiters and HR departments streamline everything from posting job openings to screening resumes, scheduling interviews, and eventually, onboarding new hires. It's like having a super-organized assistant dedicated solely to recruitment. Imagine trying to sort through hundreds (or even thousands!) of resumes manually. No thanks! ATS to the rescue.
Why is an ATS so crucial? Well, consider a company receiving an overwhelming number of applications for a single position. Without an ATS, sifting through those applications would be a monumental task, prone to human error and delays. An ATS automates much of this process, allowing recruiters to quickly identify candidates who meet specific criteria, track their progress through the hiring pipeline, and communicate with them efficiently. It's all about optimizing the talent acquisition process. Plus, it ensures compliance with various labor laws by maintaining accurate records of all applications and interactions.
Beyond mere organization, a sophisticated ATS offers features like automated email responses, interview scheduling tools, and even background check integrations. Some even use AI-powered tools to help identify the best candidates based on their skills and experience. Its not about replacing human judgment, but augmenting it with data-driven insights. Think of it as giving HR superpowers! Ultimately, an ATS helps companies find the right talent faster, more efficiently, and with less hassle. And who doesn't want less hassle?
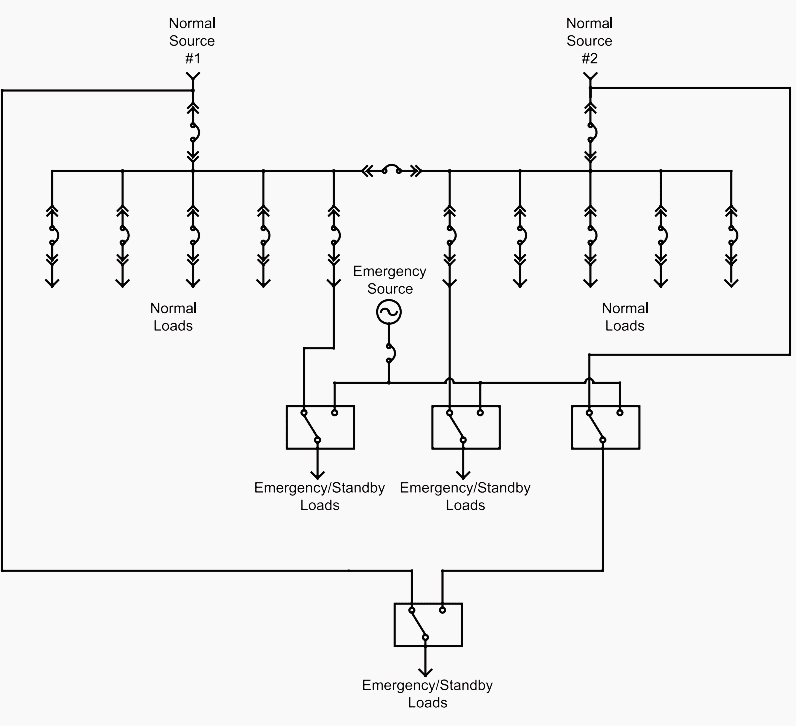
Wiring Diagrams For Ats To Generator Diagram
STS
2. Security Token Service
Now, let's switch gears entirely and delve into the world of STS, or Security Token Service. This is where things get a bit more technical, but bear with me! An STS is a critical component of identity and access management, particularly in web services and cloud environments. Essentially, it's a system that issues security tokens — digital credentials that grant users access to specific resources or services. Think of it as a digital keycard that unlocks the doors to different parts of a digital building.
Unlike an ATS, which focuses on managing the flow of job applicants, an STS focuses on controlling access to sensitive data and applications. It verifies the identity of a user or application and then issues a token containing information about their permissions and privileges. This token can then be presented to other services to prove the user's identity and authorization to access those services. In simpler terms, its like showing your ID card to get into a concert; the STS is the bouncer, and the token is your ticket.
The importance of an STS lies in its ability to centralize and secure the authentication process. Instead of each application or service having to independently verify user identities, they can rely on the STS to do the heavy lifting. This reduces complexity, improves security, and makes it easier to manage access control policies. Imagine each website requiring a completely separate login — what a headache! An STS helps streamline this process, making your online experience smoother and more secure.
Moreover, an STS enables single sign-on (SSO) functionality, allowing users to authenticate once and then access multiple applications without having to re-enter their credentials. This is a huge convenience for users and a significant security enhancement for organizations. By centralizing authentication, the STS reduces the risk of password reuse and phishing attacks. So, while you might not directly interact with an STS, its quietly working behind the scenes to protect your digital identity and access to the online world.

A Comparison Between Traditional ATS And Closed Transition [5
Key Differences in a Nutshell
3. Side-by-Side Comparison
To make things crystal clear, let's break down the core differences between ATS and STS: ATS is about talent acquisition — finding, attracting, and managing job candidates. It streamlines the hiring process and helps companies find the best fit for their open positions. STS, on the other hand, is about identity and access management — verifying user identities and granting access to resources based on their roles and permissions. It secures digital assets and ensures that only authorized users can access sensitive data.
Think of it this way: ATS is like the HR department's secret weapon for finding the perfect employee, while STS is the IT department's shield against unauthorized access. One focuses on bringing people into the organization, while the other focuses on protecting the organization from unauthorized access. They operate in completely different realms, but both are essential for a well-functioning and secure organization.
The target audience for each system is also quite different. ATS is primarily used by HR professionals, recruiters, and hiring managers. STS, on the other hand, is typically used by IT administrators, security professionals, and developers. These distinct user groups further highlight the separate roles that ATS and STS play within an organization. So, the next time you hear someone mention ATS or STS, you'll know exactly which world they're talking about!
In essence, confusing ATS and STS is like confusing a recruiter with a cybersecurity expert. Both are important, both have specialized skills, but they are in entirely different professions! Understanding the nuances of each acronym can help you navigate the tech landscape with greater confidence. Now, go forth and conquer the acronym jungle!
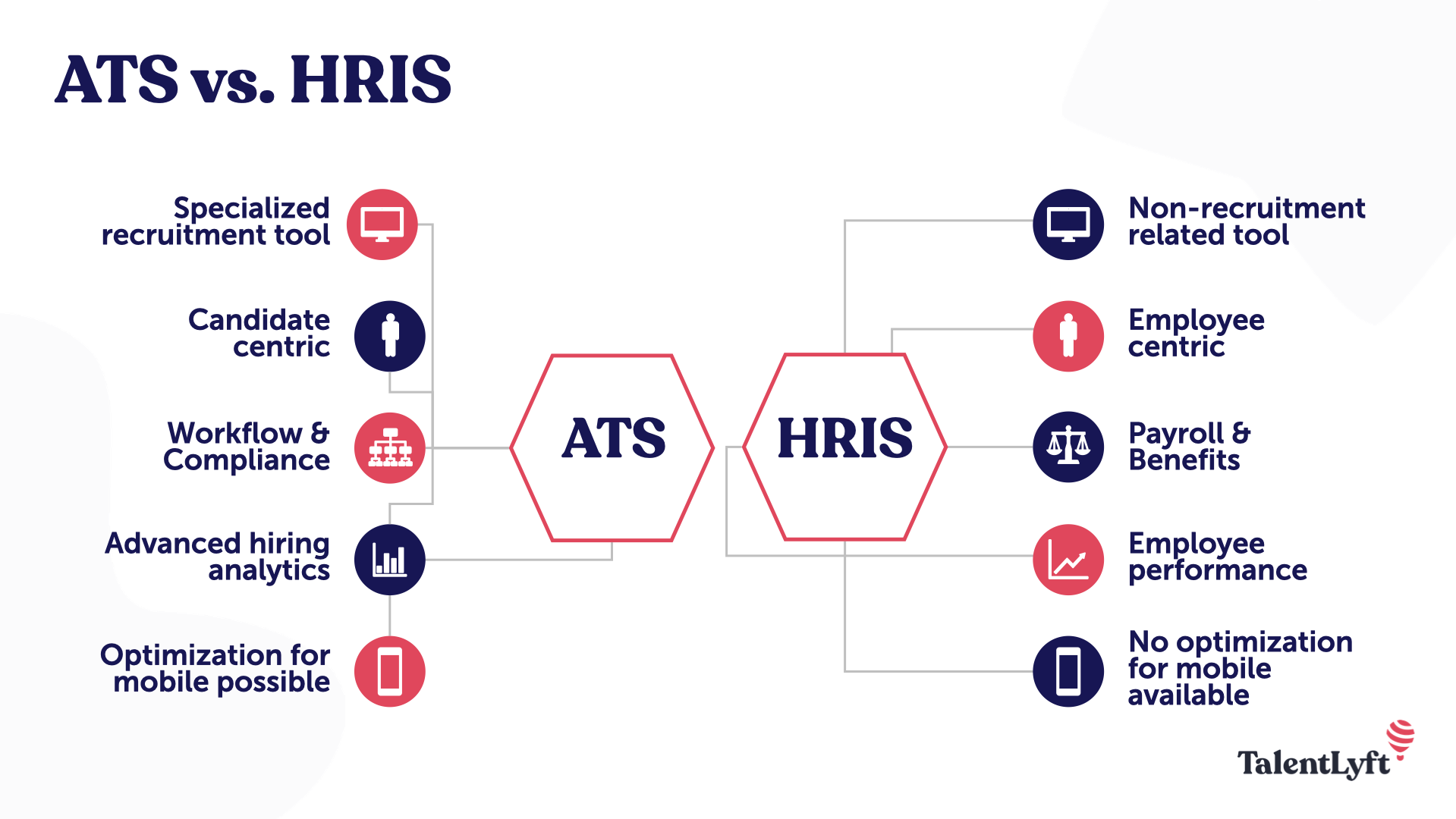
HRIS Vs. ATS你需要哪种人力资源软件解决方案? TalentLyft Bob多特蒙德体育app,bob综合体育平台下载
Why Does This Matter to You?
4. Real-World Implications
You might be thinking, "Okay, this is interesting, but how does this affect me?" Well, whether you're a job seeker or simply a user of online services, both ATS and STS play a role in your life. If you've ever applied for a job online, your resume has likely passed through an ATS. Knowing how these systems work can help you optimize your resume and cover letter to increase your chances of getting noticed.
Think about including relevant keywords that match the job description, using a clear and concise format, and highlighting your skills and accomplishments. While the ATS is the first gatekeeper, remember that a human will eventually review your application. Make sure your resume tells a compelling story and showcases your unique value proposition. In short, tailor your application to each specific job and make it easy for the ATS (and the human reviewer) to understand why you're the perfect candidate.
On the other hand, if you use online services, you're constantly interacting with STS systems, even if you don't realize it. Every time you log in to a website or application, an STS is likely verifying your identity and granting you access. A robust STS ensures that your data is protected and that only authorized users can access your account. This is particularly important in today's digital landscape, where data breaches and cyberattacks are becoming increasingly common. So, while you might not be directly involved in configuring or managing an STS, you benefit from its security features every time you use the internet.
Understanding the roles of both ATS and STS can also help you appreciate the complexity and sophistication of modern technology. These systems are constantly evolving to meet the ever-changing needs of businesses and users. By staying informed about these advancements, you can become a more savvy and informed consumer of technology. Plus, you'll have some impressive cocktail party conversation starters! Now you can confidently explain the difference between an ATS and an STS to your friends and family. Prepare to be amazed by their reactions!
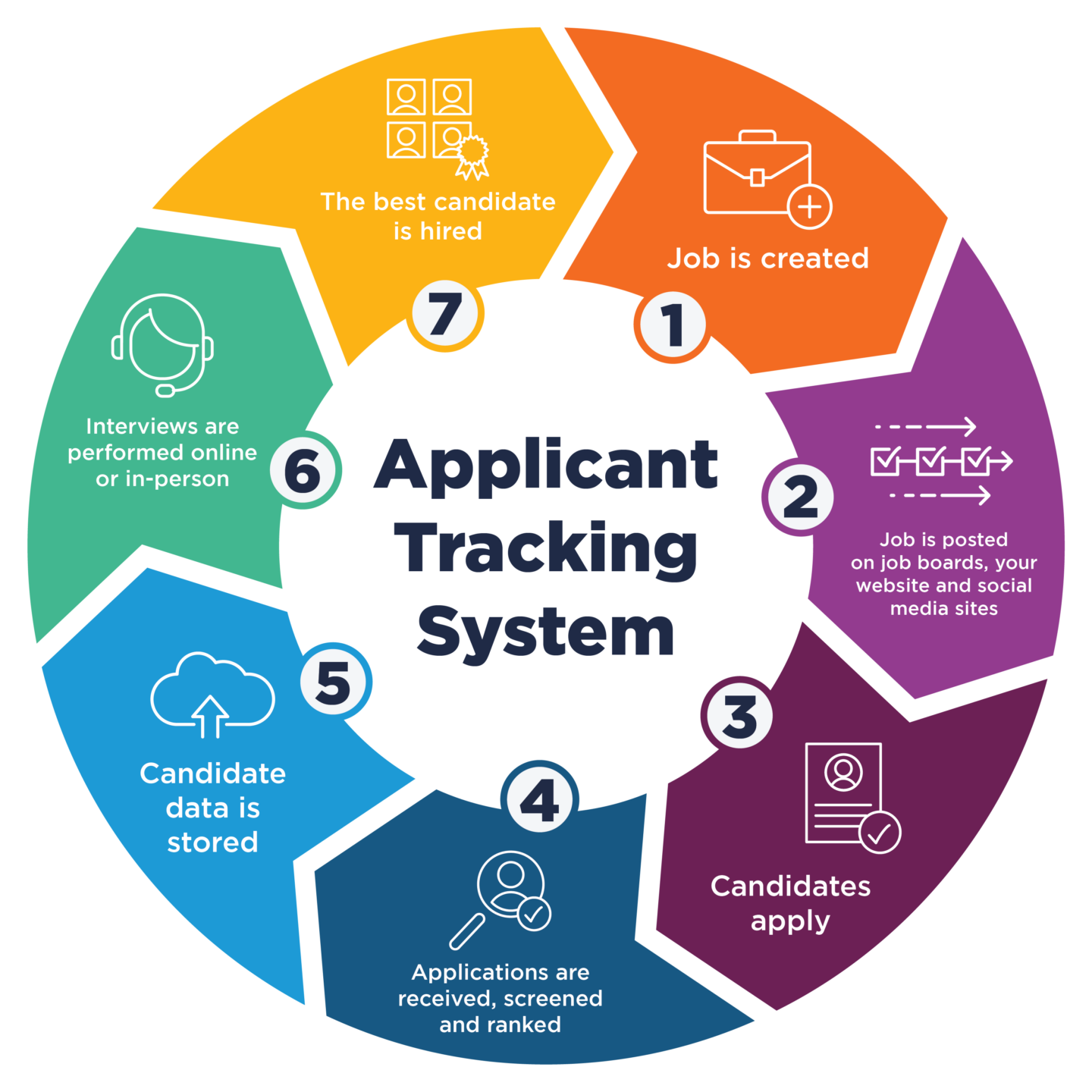
The Future of ATS and STS
5. Evolving Landscapes
The world of technology never stands still, and both ATS and STS are continually evolving to meet new challenges and opportunities. In the realm of ATS, we're seeing a greater emphasis on artificial intelligence (AI) and machine learning (ML). AI-powered ATS systems can now automatically screen resumes, identify promising candidates, and even conduct initial interviews using chatbots. This can significantly reduce the workload for recruiters and improve the efficiency of the hiring process.
However, the use of AI in ATS also raises ethical concerns, such as the potential for bias and discrimination. It's crucial that these systems are designed and used responsibly to ensure fairness and equal opportunity for all candidates. The future of ATS will likely involve a delicate balance between automation and human oversight, ensuring that technology is used to enhance, rather than replace, human judgment.
In the world of STS, we're seeing a growing adoption of blockchain technology and decentralized identity solutions. These technologies offer the potential to create more secure and privacy-preserving identity management systems. Blockchain-based STS systems can provide tamper-proof records of user identities and permissions, making it more difficult for attackers to compromise accounts. Decentralized identity solutions, on the other hand, put users in control of their own data, allowing them to selectively share their information with different services.
The future of STS will likely involve a shift towards more user-centric and privacy-focused identity management systems. These systems will empower users to control their own data and securely access online services without having to rely on centralized intermediaries. As technology continues to evolve, both ATS and STS will play increasingly important roles in shaping the future of work and the online world. Staying informed about these advancements will be crucial for navigating the ever-changing landscape of technology and ensuring a secure and equitable future for all.
![Summary Of Current ATS/STS/STR [11]. Download Summary Of Current ATS/STS/STR [11]. Download](https://www.researchgate.net/publication/356681848/figure/tbl1/AS:1098181534334976@1638838289948/Summary-of-Current-recommendations-of-ATS-STS-STR-11.png)
Summary Of Current ATS/STS/STR [11]. Download
FAQ
6. Your Burning Questions Answered
Still have some lingering questions? Let's tackle some frequently asked questions about ATS and STS:
Q: Are ATS systems only used by large companies?
A: Not at all! While large companies often rely heavily on ATS systems to manage high volumes of applications, smaller businesses can also benefit from using these tools. There are many affordable and user-friendly ATS solutions designed specifically for small to medium-sized businesses (SMBs). These systems can help SMBs streamline their hiring processes, improve candidate tracking, and ultimately find the best talent for their teams.
Q: How can I optimize my resume for ATS?
A: Great question! Here are a few tips: Use relevant keywords from the job description, use a clear and concise format, avoid using tables or images, and save your resume as a PDF file. Also, proofread carefully for any typos or grammatical errors. Remember, the goal is to make your resume easy for the ATS to parse and for the human reviewer to understand.
Q: Is STS only used for web applications?
A: While STS is commonly used for web applications, it can also be used for other types of applications, such as mobile apps and desktop software. The key requirement is that the application needs to authenticate users and control access to resources. STS provides a centralized and secure way to manage this authentication process, regardless of the type of application.
Q: What are the biggest security risks associated with STS?
A: Like any security system, STS is not immune to risks. Some of the biggest risks include: Token theft or compromise, weak or compromised authentication credentials, and vulnerabilities in the STS software itself. It's crucial to implement strong security measures, such as multi-factor authentication and regular security audits, to mitigate these risks and ensure the integrity of the STS system.